Ransomware Defense – Incident Recovery: Why File and Device Quarantine is a Must-Have!

In recent years, ransomware attacks have emerged as one of the major cyber threats facing businesses and organizations. These assaults have the power to bring down whole networks and systems, compromise sensitive information, and result in enormous financial losses. These breaches can have a disastrous effect on businesses beyond just financial losses, resulting in data loss, defamation, penalties, and the list goes on. Ransomware attacks are now occurring more frequently, with one occurring every 11 seconds, according to recent studies. The cost of these attacks is anticipated to soar to an astounding $20 billion by 2025, according to Cybersecurity Ventures’ 2021 Ransomware Report. Implementing efficient measures to lessen the effects of ransomware attacks is essential given the high stakes involved.
Increasingly, CISOs are making Ransomware Defense and Data Resiliency core of their Cybersecurity posture. Afterall, when all other measures have failed and a breach has occurred, the fall back, the last line of defense is Recovering seamlessly from the attack and getting back to business as usual.
During an Incident Recovery, there are several challenges. There are several different teams involved and getting them aligned is a challenge. The IT team, data recovery team, and incident response team are the ones responsible for bringing back the organization to normalcy. While investigations are going on, the data recovery team is looking to bring the data back to get the business back on its feet. As a result, it is important that infected files, folders, and devices that are under investigation or tagged as infected shouldn’t get recovered into the mainstream. A small misstep during recovery can bring all efforts to naught.
Wouldn’t it be great if you could have the assurance that any file or device identified as infected is blocked out from being accessed or copied over?! The solution is File and Device Quarantine. By doing so, you might be able to limit the harm that attacks do and stop malware from spreading. In this blog, we’ll dive into what file and device quarantine is, how it works, and how it can help keep your systems safe from ransomware attacks.
Understanding File and Device Quarantine
Have you ever thought about ways that businesses could stop ransomware from spreading and lessen the damage?
The answer lies in file and device quarantine, a critical component of a comprehensive ransomware defense strategy. By isolating potentially malicious files or devices, organizations can prevent the spread of malware and limit the damage caused by ransomware attacks.
File and device quarantine works by placing malicious files or devices in a secure, isolated environment where they cannot interact with other parts of the system. This prevents the spread of malware and helps contain the damage caused by ransomware attacks. Quarantine can be automated or manual, depending on the specific tools and processes used.
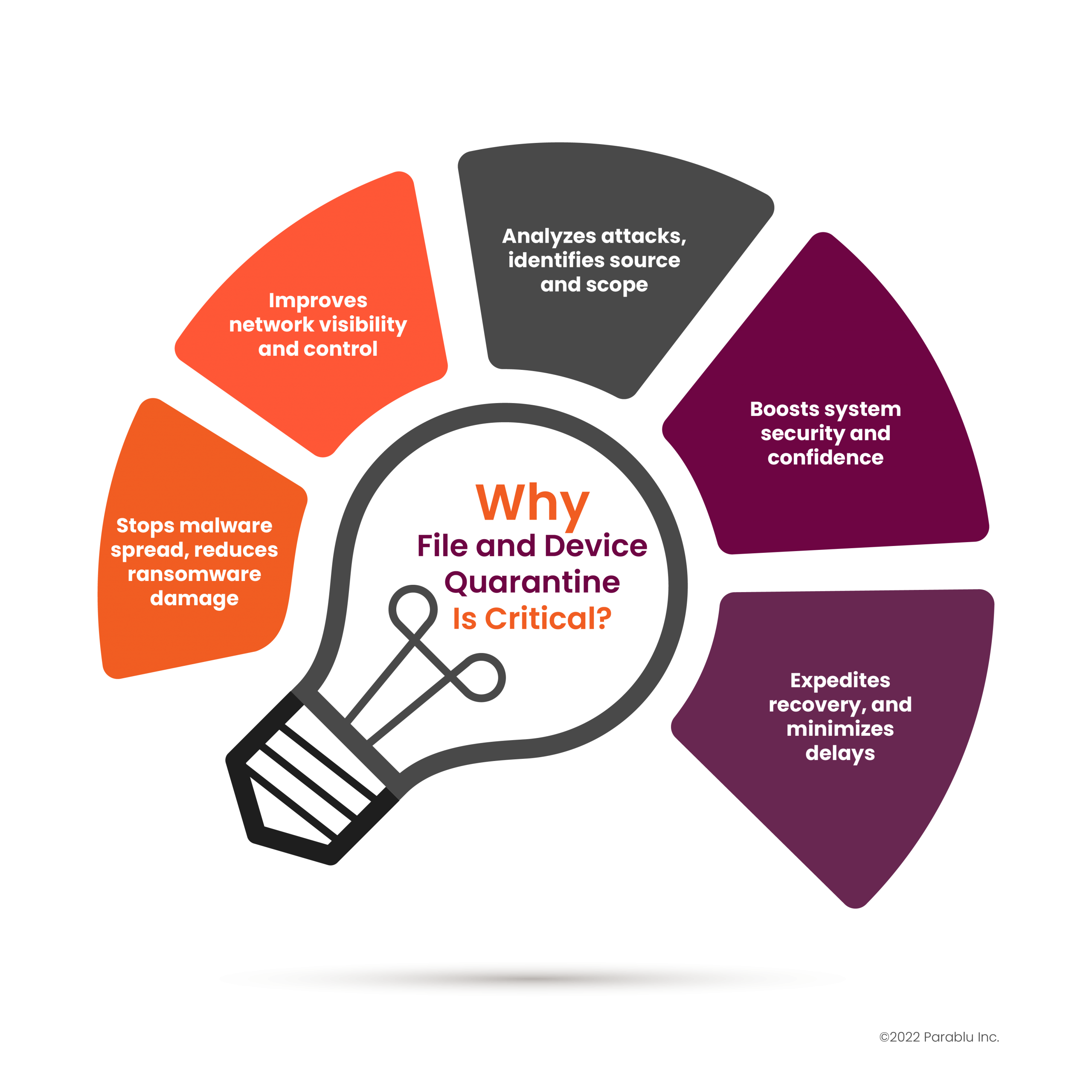
The benefits of file and device quarantine include:
- Prevention of malware from spreading to other parts of the system
- Reduction of the potential damage caused by ransomware attacks.
- Improved visibility and control over the network, across teams.
- Facilitation of analysis to identify the source and scope of the attack.
- Greater confidence in the security and integrity of the system.
- Faster recovery to normalcy reducing delays and duplicated efforts.
Overall, file and device quarantine is an essential tool for preventing and mitigating the impact of ransomware attacks. By isolating potentially malicious files and devices, organizations can limit the damage caused by these attacks and maintain the integrity of their systems.
The Importance of File and Device Quarantine
Are you aware of the risks associated with inadequate file and device quarantine measures? Failing to quarantine infected files and devices can result in severe consequences, including the propagation of malware, data loss, system downtime, and legal liability. These risks are not just hypothetical – numerous high-profile cases have highlighted the real-world consequences of inadequate quarantine measures. For example, the NotPetya attack, Equifax data breach, and Target data breach all resulted in significant financial losses, reputational damage, and legal consequences. To protect your organization’s critical systems and data from harm, it’s crucial to implement effective quarantine measures for infected files and devices.
Implementing Effective File and Device Quarantine with Parablu’s BluVault
Imagine a scenario where a company has experienced a major cyber-attack. Different teams are working tirelessly to recover from the incident and get back to business as usual. Under immense pressure, every second counts, and any delay can result in significant financial loss and reputational damage.
During this recovery process, it is crucial to ensure that access to infected files is locked out to prevent any further damage. Even if these files cannot be restored or recovered, they still pose a threat to the organization’s security and must be handled with extreme caution. This is where Parablu’s BluVault comes in with its robust file and device quarantine functionality.
BluVault’s quarantine feature helps to reduce the risk of false positives in identifying infected files and devices. It tags potentially infected files and devices and prevents them from being backed up or synced to the cloud, thus ensuring that only clean and curated data is recovered. By doing so, it reduces the time and effort required for data recovery, minimizing downtime, and reducing the impact of data loss on the organization’s operations.
BluVault’s Prepare, Prevent, Detect, and Recover stages of the Data Resiliency lifecycle provide comprehensive backup and recovery capabilities and robust security features to help organizations critical data protection from cyber threats. By implementing effective file and device quarantine measures, organizations can ensure the integrity of their data and prevent further damage from cyber-attacks.
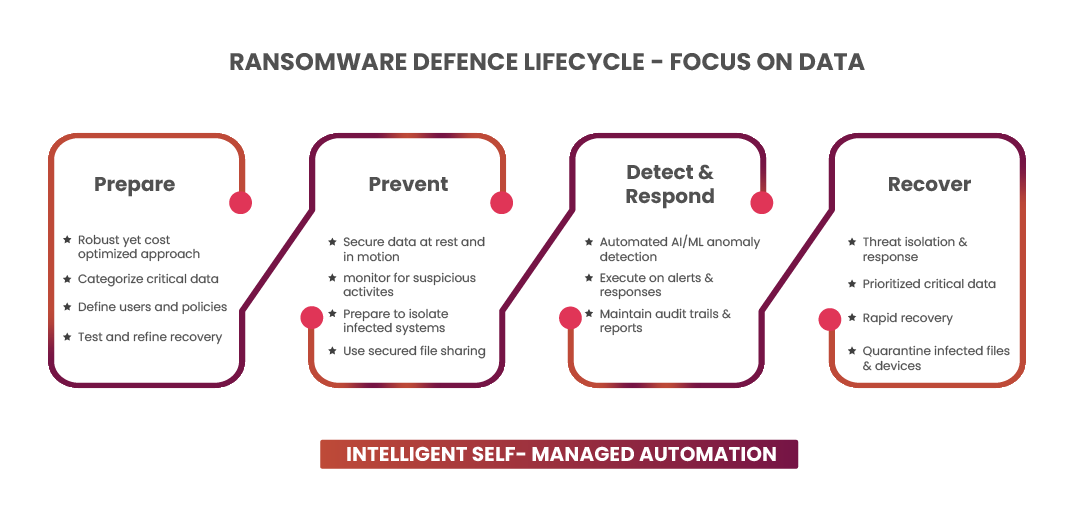
In summary, Parablu’s BluVault is considered central to an organization’s cybersecurity strategy as preparing to have the last line of defense and specifically during an incident recovery. Its file and device quarantine feature helps to prevent the spread of malware and other cyber threats, allowing organizations to recover quickly and minimize the impact of data loss on their operations. By implementing effective quarantine measures, organizations can ensure that their critical data is protected, and their reputation remains intact.
Best Practices for File and Device Security Against Ransomware
In this section, we will discuss the best practices that organizations can follow to ensure that their files and devices are secured from malicious attacks. These measures include:
- Conduct regular backups and store them securely off-site.
- Educate employees on best practices for file and device quarantine.
- Use software solutions like Parablu’s BluVault for secure cloud-based backup and recovery.
- Implement device management policies that restrict personal device use and allow remote wipe capabilities.
- Have an incident response plan in place to quickly isolate infected devices and restore data from backups.
File and device quarantine is a differentiating component of any ransomware defense solution.
By adhering to the best practices highlighted throughout this article, such as maintaining regular backups, providing employee education on cybersecurity, implementing device management policies, and developing a robust incident response plan, organizations can significantly minimize their risk of falling victim to a security breach. However, it is vital to recognize that solely relying on preventive measures is not enough. A resilient data protection solution, like Parablu’s BluVault, that includes robust file and device quarantine capabilities, serves as the last line of defense against ransomware attacks.
Therefore, it is crucial for businesses to prioritize their ransomware defense efforts and proactively implement effective quarantine measures. By doing so, organizations can fortify their data security posture and ensure the continuity and integrity of their valuable information in the face of evolving cyber threats.
Final Words:
In conclusion, the urgency for businesses to act is paramount in the face of inevitable attacks. Parablu’s BluVault Ransomware Defense Suite offers a comprehensive solution that consolidates all essential elements, making it user-friendly for both administrators and users. From proactive measures like identifying sensitive data and implementing user access controls to ensuring secure backups in encrypted cloud vaults, detecting unusual activities, and enabling swift recovery with file and device quarantine, BluVault addresses the previously burdensome and unreliable aspects of data security. With audit-ready reports for investigations and compliance, Parablu’s commitment to safeguarding data from ransomware attacks is unwavering. Choosing BluVault means embracing a secure and protected future for your valuable data.









