Data Resiliency and Ransomware Defense, at the core of your Cybersecurity Posture

The increasing frequency and severity of cyberattacks and data breaches have emphasized the importance of having a strong cybersecurity posture. A cybersecurity posture is an organization’s comprehensive approach to managing and protecting its digital assets and information from unauthorized access, theft, and damage. A comprehensive cybersecurity posture across people, process, and tools is critical in today’s digital landscape. This posture should be integrated throughout the development and deployment lifecycle, from the planning stages to the end-of-life of applications and systems.
People are an essential part of a comprehensive cybersecurity posture. Employees should be trained regularly on cybersecurity best practices, including how to identify and avoid phishing attacks and the proper handling of sensitive data. Additionally, organizations should establish policies and procedures for employee onboarding and offboarding to ensure that access to systems and data is granted only to authorized individuals.
Processes are equally important in a comprehensive cybersecurity posture. Organizations should establish processes for vulnerability management, incident response, and disaster recovery. These processes should be regularly reviewed and updated to ensure their effectiveness in addressing emerging threats.
Tools are critical components of a comprehensive cybersecurity posture. Organizations should deploy security tools, such as firewalls, intrusion detection and prevention systems, and antivirus software, to protect against cyber threats. Additionally, organizations should implement identity and access management tools to ensure that only authorized individuals have access to critical systems and data.
A secure development lifecycle (SDL) is an essential component of a comprehensive cybersecurity posture. The SDL is a process that integrates security considerations throughout the software development lifecycle. By integrating security into the development process, organizations can reduce the risk of vulnerabilities in their applications and systems.
DevOps is an approach that integrates software development and operations, allowing for the rapid development and deployment of software. DevOps is an excellent way to streamline the development process, but it can also introduce security risks. To address these risks, organizations should implement DevSecOps, which integrates security into the DevOps process. By incorporating security into DevOps, organizations can reduce the risk of vulnerabilities in their applications and systems.
Zero-trust and zero-privacy principles are essential components of a comprehensive cybersecurity posture. Zero-trust security assumes that every user and device is potentially hostile, and access to systems and data is granted only to authorized individuals. This approach minimizes the risk of unauthorized access and data breaches. Zero-privacy is a security principle that emphasizes the protection of personal data, and the minimization of data collection and storage. By implementing zero-privacy principles, organizations can minimize the risk of data breach and unauthorized access to sensitive data.
Cloud backup and rapid restore are essential tools in ensuring data resiliency and protection against ransomware attacks. Cloud backup enables organizations to store their data securely and recover it quickly in the event of a disaster or cyber-attack. Rapid restore is a process that enables organizations to quickly recover data in the event of a ransomware attack. By having a comprehensive disaster recovery plan in place that includes cloud backup and rapid restore, organizations can reduce the impact of a ransomware attack and ensure business continuity.
As more and more organizations digitize their operations, data has become the lifeblood of businesses. However, with this increased reliance on data comes the risk of data loss or theft due to cyber-attacks, hardware failure, or human error. Ensuring data resiliency and ransomware defense should be an integral part of every organization’s comprehensive cybersecurity posture.
Data resiliency refers to an organization’s ability to recover data quickly and effectively in the event of data loss. It is crucial to implement best practices for data resiliency, including regular backups of data and storing them in a secure location, preferably offsite. Additionally, testing backups regularly and having a comprehensive disaster recovery plan in place will help ensure that critical data can be recovered quickly in the event of a disaster or cyber-attack. Organizations should classify their data according to its level of sensitivity and importance, and appropriate measures should be taken to recover it in the event of a disaster.
Data resiliency refers to an organization’s ability to recover data quickly and effectively in the event of data loss.
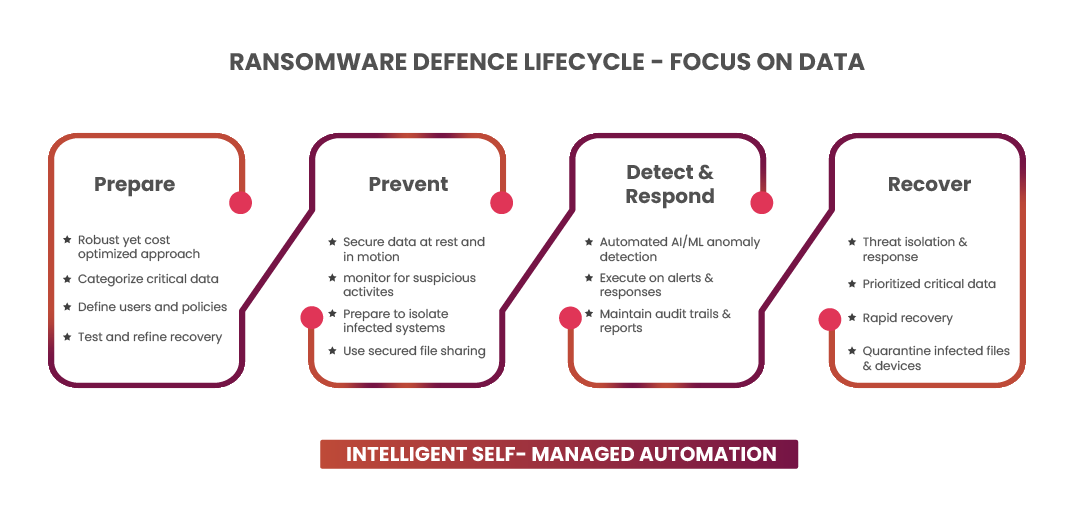
There are several best practices organizations can implement to ensure data resiliency, including:
1. Regular backups: Organizations should perform regular backups of their data and store them in a secure location, preferably offsite, to ensure that data can be recovered quickly in the event of a disaster or cyber-attack.
2. Test backups: It is crucial to test backups regularly to ensure they are working correctly, and that data can be restored in a timely and efficient manner.
3. Disaster recovery plan: Organizations should have a comprehensive disaster recovery plan in place that outlines the steps to be taken in the event of a data loss or cyber-attack. This plan should be regularly updated and tested to ensure its effectiveness.
4. Data classification: Organizations should classify their data according to its level of sensitivity and importance. This classification will help ensure that critical data is given the highest level of protection and that the appropriate measures are taken to recover it in the event of a disaster.
Ransomware attacks have become one of the most significant cybersecurity threats to organizations. In a ransomware attack, cybercriminals encrypt an organization’s data and demand a ransom payment to provide the decryption key. To ensure effective ransomware defense, organizations should take the following steps:
1. Regularly update software: Organizations should regularly update their software, including operating systems, applications, and security software, to ensure that they are protected against the latest threats.
2. Train employees: Employees are often the weakest link in an organization’s cybersecurity posture. Therefore, organizations should regularly train their employees on best practices for cybersecurity, including how to identify and avoid phishing attacks.
3. Use multifactor authentication: Multifactor authentication is a security measure that requires users to provide more than one form of authentication to access data or systems. This added layer of security can help prevent unauthorized access to sensitive data.
4. Implement access controls: Access controls can help prevent ransomware attacks by limiting the access of users to sensitive data. Organizations should ensure that only authorized users have access to critical data, and that access controls are regularly reviewed and updated.
Parablu’s data resiliency solution
Parablu offers a data resiliency solution that can help organizations enhance their cybersecurity posture by providing a secure and efficient way to protect their data. The solution uses advanced encryption technology and secure data transfer protocols to store and backup data to the cloud, making it accessible only to authorized users.
By implementing Parablu’s data resiliency solution, organizations can ensure their data remains backed up and protected even in the event of a security incident. The solution leverages automated backup and recovery processes, real-time monitoring, and alerts, as well as advanced encryption technology, to provide a reliable and efficient way to secure data.
BluVault, Parablu’s data resiliency solution, is designed to provide a highly secure and efficient way to backup, restore, and recover data in the cloud. BluVault offers businesses a range of features that make it stand out from other data backup and recovery solutions. For instance, BluVault is infrastructure-agnostic, meaning it can integrate seamlessly with existing access controls, data flows, and storage.
BluVault works closely with Active Directory and Azure Active Directory access controls, making it easy to manage and control user access to data, while integrating with existing data flows and storage solutions. Businesses can also outsource their data backup and recovery processes to Parablu with Backup as a Service (BaaS), ensuring their data is backed up securely and efficiently.
Parablu’s data resiliency solution is a central to ransomware defense. Ransomware attacks are increasingly common and can be devastating to businesses, resulting in data loss and downtime. With Parablu’s data resiliency solution, organizations can quickly restore their data to a pre-attack state and minimize the impact of a ransomware attack.
Parablu’s data resiliency solution as ransomware defense

Parablu’s data resiliency solution provides organizations with a secure and efficient way to protect their data, ultimately enhancing their cybersecurity posture as a defense against ransomware. The solution leverages advanced encryption technology and secure data transfer protocols to securely store and backup data to the cloud. This ensures that data remains accessible only to authorized users.
By implementing Parablu’s data resiliency solution, organizations can rest assured that their data is always backed up and protected, even in the event of a security incident. This is achieved using advanced encryption technology, automated backup and recovery processes, and real-time monitoring and alerts.
Overall, Parablu’s data resiliency solution is a valuable tool for organizations looking to enhance their cybersecurity posture by securing their data. It provides a reliable and efficient way to backup and protect data, reducing the risk of cyber threats and ensuring business continuity.
BluVault – Parablu’s Data Resiliency Solution
BluVault, developed by Parablu, is a data resiliency solution designed to provide a highly secure and efficient way to backup, restore, and recover data in the cloud. BluVault provides a highly secure data backup and recovery solution that helps organizations protect their data from loss, theft, and damage. With BluVault, organizations can easily backup their data to multiple cloud destinations, ensuring that their data is always protected and available. It uses advanced encryption algorithms and security protocols to ensure that the data is stored securely and is accessible only to authorized personnel. The solution offers a range of features that make it stand out from other data backup and recovery solutions.
Infrastructure agnostic / integrates closely with existing access controls (AD/AAD), data flows and storage. BaaS as an option for end-to-end secure data resiliency:
One of the key features of BluVault is its infrastructure-agnostic approach. This means that it can integrate seamlessly with existing access controls, data flows, and storage. BluVault works closely with Active Directory (AD) and Azure Active Directory (AAD) access controls, making it easy to manage and control user access to data. This integration ensures that only authorized personnel can access the data, improving data security.
Moreover, BluVault integrates with existing data flows, making it easy for businesses to manage their data backup and recovery processes without disrupting existing data flows. BluVault also integrates with existing storage solutions, giving businesses the flexibility to store their data in their preferred cloud storage provider.
BluVault also offers Backup as a Service (BaaS), providing end-to-end secure data resiliency. With BaaS, businesses can outsource their data backup and recovery processes to Parablu, ensuring that their data is backed up securely and efficiently.
BluVault, offers businesses a highly secure and efficient way to backup, restore, and recover their data in the cloud.
Zero Knowledge Privacy
BluVault by Parablu offers a Zero-Knowledge Privacy feature that ensures maximum privacy and security for businesses. This feature encrypts and stores all data securely, with only authorized personnel having access to the decryption keys. Parablu has no access to the data, providing businesses with an added layer of protection against unauthorized access and breaches. BluVault’s Zero-Knowledge Privacy feature is a valuable tool for businesses storing sensitive data, ensuring that their data remains safe and secure.
Zero Trust Security
BluVault’s Zero-Trust Security feature is a game-changer in ensuring maximum security for businesses. This feature assumes that every user, device, or system requesting access to data is a potential threat, even if the request is coming from within the network. BluVault thoroughly verifies every request for access to data, ensuring that only authorized personnel have access to the data. This approach minimizes the risk of a data breach or unauthorized access, providing an added layer of protection for businesses. With the Zero-Trust Security feature of BluVault, businesses can rest assured that their critical data is always secure.
Industrial-strength Encryption, BYOK
Parablu’s data resiliency solution offers industrial-strength encryption with the Bring Your Own Key (BYOK) feature, providing businesses maximum security and control over their data. BYOK allows businesses to bring their own encryption keys, giving them complete control over the encryption and decryption process, ensuring that only authorized personnel have access to the decryption keys, reducing the risk of unauthorized access or data breaches. With industrial-strength encryption, businesses can rest assured that their data is safe and secure, and the BYOK feature of BluVault provides an added layer of protection, giving businesses complete control over the encryption and decryption process, ensuring that their critical data is always secure.
File and Device Quarantining
BluVault’s File and Device Quarantining feature adds an extra layer of security to businesses’ cybersecurity posture by allowing them to quarantine suspicious or potentially harmful files and devices. When a file or device is flagged, it is isolated from the rest of the network, preventing any potential threats from spreading. This feature ensures that businesses can quickly and easily respond to potential threats, reducing the risk of data breaches or unauthorized access. With File and Device Quarantining, businesses can rest assured that their data is always secure, even in the face of potential threats.
Unusual Activity Detection
BluVault’s Unusual Activity Detection feature is a real-time alert system that continuously monitors data backup and recovery activities to detect any suspicious or unusual activity. This proactive tool is crucial for businesses looking to safeguard their sensitive data from security threats and keep their operations running smoothly, providing early detection of potential data breaches or unauthorized access. By using this feature, businesses can take immediate action to prevent further damage and stay ahead of potential security threats, ensuring the safety and security of their critical data.
Rapid Restores during Ransomware Recovery
BluVault provides businesses with a Rapid Restores feature focused on Ransomware Recovery. With this feature, businesses can quickly retrieve their data to a previous point in time before a ransomware attack occurred, minimizing downtime, and mitigating the impact of the attack. By using advanced backup and recovery techniques, such as incremental backups and point-in-time restores, businesses can recover their data accurately and promptly.
The Rapid Restores feature is essential for businesses that prioritize the protection of their critical data from ransomware attacks. Its fast data retrieval process enables businesses to quickly resume their operations, maintaining their reputation and trust. In conclusion, BluVault’s Rapid Restores feature is a valuable tool for businesses seeking an efficient and reliable data retrieval process, while mitigating the impact of ransomware attacks.
Litigation Hold
Parablu’s BluVault solution offers a Litigation Hold feature that ensures businesses maintain their data’s original state, prohibiting any changes or deletion during legal proceedings. This feature offers a secure and cost-effective solution for managing legal holds, automating the data preservation process, and enabling businesses to efficiently manage their legal holds.
BluVault’s Litigation Hold feature guarantees the preservation of data in its original state, reducing the risk of legal sanctions or penalties. It ensures compliance with legal and regulatory data preservation and retention requirements, reducing the probability of human error. In summary, BluVault’s Litigation Hold feature is an essential tool for businesses seeking a secure and efficient way to manage their legal holds, protecting their data during legal proceedings.
Closing Remarks
In conclusion, data resiliency and ransomware defense should be a top priority for every organization’s comprehensive cybersecurity posture. By implementing best practices for data resiliency and taking steps to protect against ransomware attacks, organizations can reduce the risk of data loss and theft, protect their reputation and financial stability, and ensure business continuity. With focus on data at the core of the overarching cybersecurity posture, it’s not a matter of if an organization will be attacked, but when, so being prepared and proactive is key to protecting sensitive data and ensuring business continuity.
Parablu’s data resiliency solution is a valuable tool for organizations looking to enhance their cybersecurity posture by securing their data. The solution offers a reliable and efficient way to backup and protect data, reducing the risk of cyber threats and ensuring business continuity. Additionally, BluVault’s infrastructure-agnostic approach, integration with existing data flows and storage solutions, and Backup as a Service option make it a standout data backup and recovery solution.









